dibuka Program Training Online / Webinar !
Tetap bisa training sekalipun #diRumahAja
PUBLIC TRAINING - PURNAMA ACADEMY
Kami Bekerjasama dengan hotel bintang di 4 kota Bandung-Jakarta-Bali-Cikarang untuk memberikan kenyamanan peserta public training
REQUEST FOR INHOUSE TRAINING
Inhouse Training adalah pilihan paling tepat untuk jumlah peserta perusahaan yang banyak dengan mengutamakan efisiensi biaya training.
PORTFOLIO : INHOUSE TRAINING ANDROID - PLN MALUKU
Inhouse Training Android Application Development di PT. PLN Wilayah Maluku selama 4 hari
PORTFOLIO : INHOUSE TRAINING MAGENTO - INFOTECH JAKARTA
Inhouse Training Magento E-Commerce berdurasi 7 hari dibagi 2 sesi Fundamental dan Advanced.
Monday, October 10, 2022
EXAM PREPARATION - CDMP DMBOK
WHAT IS CTFL ISTQB
TRAINING CENTER - CDPSE ISACA
SCHEDULES - CISA ISACA (Certified Information Systems Auditor)
Friday, October 7, 2022
SCHEDULES
TEMPAT PELATIHAN ITIL V.4
WHAT IS COBIT ISACA
Wednesday, September 28, 2022
TIPS ITIL
ITIL terdiri dari serangkaian buku memberikan bimbingan pada penyediaan kualitas layanan TI, dan pada akomodasi dan fasilitas yang diperlukan untuk mendukung lingkungan TI. ITIL telah dikembangkan sebagai pengakuan ketergantungan organisasi 'tumbuh di TI dan mewujudkan praktik terbaik untuk IT Service Management.
PURNAMA ACADEMY :
Informasi, Silabus & Pendaftaran
Hubungi
Purnama Academy
Whatsapp : 081-223344-506
WHATS IS TOGAF?
TOGAF is a framework for enterprise architecture that provides an approach for designing, planning, implementing and governing an enterprise architecture. TOGAF 9.2 certification is a trusted and vendor-neutral certification which ensures enterprise architecture professionals share the same standards across the world.
PURNAMA ACADEMY :
Informasi, Silabus & Pendaftaran
Hubungi
Purnama Academy
Whatsapp : 081-223344-506
Tuesday, September 27, 2022
What is COBIT (Control Objectives for Information and Related Technologies)?
COBIT is an IT governance framework for businesses wanting to implement, monitor and improve IT management best practices. COBIT is the acronym for Control Objectives for Information and Related Technologies.
The COBIT framework was created by ISACA to bridge the crucial gap between technical issues, business risks and control requirements.
COBIT can be implemented in any organization from any industry to ensure quality, control and reliability of information systems.
In the United States, COBIT is the most commonly used framework for achieving compliance with the Sarbanes-Oxley Act (SOX).
source :https://www.techtarget.com/searchsecurity/definition/COBIT
PURNAMA ACADEMY :
Informasi Silabus & Pendaftaran
Hubungi
Hery Purnama
Whatsapp : 0838-08380001
Whats is CISA ISACA
Informasi Silabus & Pendaftaran
Hubungi
Hery Purnama
Whatsapp : 0838-08380001
Monday, September 26, 2022
risk management definition
Risk management is the process of identifying, assessing and controlling threats to an organization's capital and earnings. These risks stem from a variety of sources including financial uncertainties, legal liabilities, technology issues, strategic management errors, accidents and natural disasters.
A successful risk management program helps an organization consider the full range of risks it faces. Risk management also examines the relationship between risks and the cascading impact they could have on an organization's strategic goals.
PURNAMA ACADEMY :
Informasi Silabus & Pendaftaran
Hubungi
Purnama Academy
whatsapp : 0838-0838-0001
TIPS UJIAN CGEIT
Halo semuanya. Saya berharap teman-teman semua sehat dan bahagia selalu ya. Dengan rendah hati saya sampaikan bahwa mulai bulan ini saya mendapatkan gelar CGEIT (Certified in the Governance of Enterprise IT). Saya berkomitmen untuk selalu menuliskan tips lulus setiap ujian sertifikasi yang saya ikuti sebagai ungkapan kesyukuran dan juga untuk membantu setiap kandidat ujian sertifikasi di luar sana. Jadi, inilah tips lulus ujian CGEIT versi saya :
(P.S.: beberapa di antaranya mirip dengan tips untuk lulus ujian CISA yang diposting sebelumnya karena saya yakin keduanya memerlukan persiapan yang serupa)
1. Kalibrasi Ulang Pola Pikir
Satu hal yang paling saya sadari dari materi CGEIT adalah sudut pandang dan cara berpikirnya sedikit berbeda dari yang saya miliki. Sementara sebagai praktisi terkadang saya harus berpikir praktis, ujian CGEIT mengharuskan kita untuk berpikir secara strategis dan ideal. Jadi sebelum memulai perjalanan belajar, saya mengkalibrasi ulang pola pikir. Saya juga mempersiapkan diri untuk berpikir berdasarkan peran yang diberikan misalnya komite audit, CIO, CEO, dll, serta memahami jargon/istilah yang digunakan oleh mereka.
2. Pelajari CGEIT Review Manual dan CGEIT Review Questions, Answers & Explanations Manual (QAE)
Seperti yang saya sebutkan dalam post tentang tips ujian CISA, review manual dan QAE adalah dua referensi sakral untuk semua orang yang ingin meraih sertifikasi ISACA. Luangkan waktu untuk membaca kedua buku ini dari sampul ke sampul terutama QAE karena memperkenalkan kita pada jenis pertanyaan yang akan kita hadapi. Pahami penjelasan dari jawaban-jawaban yang disarankan buku tersebut untuk mendapatkan logika, perspektif, dan kearifan yang ditetapkan ISACA. Saya juga mengidentifikasi kesenjangan pengetahuan saya dan membuatnya menjadi catatan. Saya membacanya lagi saat waktu luang.
PURNAMA ACADEMY :
Informasi Silabus & Pendaftaran
Hubungi
Purnama Academy
Whatsapp : 0838-0838-0001
Wednesday, September 14, 2022
SYLLABUS PROJECT MANAGEMENT WITH PRINCE2 AGILE
PROJECT MANAGEMENT WITH PRINCE2 AGILE KANBAN |
DESCRIPTION :
PRINCE2 is a structured project management method and practitioner certification programme. PRINCE2 emphasises dividing projects into manageable and controllable stages. It is adopted in many countries worldwide, including the UK, Western European countries, and Australia
WHAT IS AGILE KANBAN Developed by Toyota in the late 1940s, the Kanban system originally aimed to improve manufacturing efficiency. Taking its name from the card system that tracks production in a factory, it has since been refined and customised by many different manufacturers. Now, this system is used in project management, featuring in the PRINCE2 Agile guidance
OBJECTIVES :
• Understand how to manage project with PRINCE 2
• Understand how sofftware development Project works with PRINCE 2 Agile
• Understand how to use Kanban
• Understand how to Javanet Kanban SQA Tool to manage project
AUDIENCE :
• Project Manager
• SQA Project Management Team
• IT Staff
• Public
PREREQUISITES :
- Basic Knowledge in Project Management
• PART A
An Overview of PRINCE2 Agile
Principles
Continued Business Justification
Learn from Experience
Defined Roles and Responsibilities
Manage by Stages
Manage by Exception
Focus on Products
Tailor to Suit the Project Environment
Themes
Business Case
Organization
Quality
Plans
Risk
Change
Progress
Processes
Starting up a Project
Initiating a Project
Directing a Project
Controlling a Stage
Managing Product Delivery
Managing a Stage Boundary
Closing a Project
Management Products
Baselines
Benefits Management Approach
Business Case
Communication Management Approach
Configuration Management Approach
Plan
Product Description
Project Brief
Project Initiation Documentation
Project Product Description
Quality Management Approach
Risk Management Approach
Work Package
Records
Configuration Item Record
Daily Log
Issue Register
Lessons Log
Quality Register
Risk Register
Reports
Checkpoint Report
End Project Report
End Stage Report
Exception Report
Highlight Report
Issue Report
Lessons Report
Product Status Account
Roles and Responsibilities
PRINCE2 Roles
Project Board
Executive
Senior Supplier
Senior User
Project Manager
Team Manager
Project Assurance
Change Authority
Project Support
Additional Roles
Customer Subject Matter Expert
Customer Representative
Supplier Subject Matter Expert
Supplier Representative
Delivery Team Quality Assurance
Extra Concepts
Behaviors
Health Check
Cynefin
Targets
Guidance Points
Definition of Done
User Stories
The Focus Areas
The Agilometer
Requirements
Frequent Releases
Contracts
Rich Communication
Information Radiators
Daily Standups
Review Meetings
Retrospective Meetings
• PART B
Prince2 Agile Kanban
What is Kanban
Kanban Purpose
How Does Kanban Works
Using Kanban in Prince2 Agile
• PART C
Practice Prince 2 Agile Kanban with Kanban SQA Tool
Introduction
Users and Groups
Boards
Projects
Tasks
Subtasks
Swimlanes
Automatic Actions
Project Analytics
Time Tracking
Notifications
RSS/Atom Subscriptions
iCalendar Subscriptions
Settings
Advanced Search Syntax
Markdown Syntax
Keyboard Shortcuts
WHAT IS CISM ISACA-PURNAMA ACADEMY TRAINING
The CISM is meant for existing or aspiring managers, and is growing in relevance as cybersecurity at the enterprise level increasingly is becoming a c-level and board initiative. The thinking behind this certification is that as programs and needs grow, professionals will require management credentials alongside the various technical certifications that exposure to a large enterprise cybersecurity operation would require.
The Information Systems Audit and Control Association, which is known only by its acronym ISACA, is an international professional association that sponsors the CISM. The certification requirements include five years experience in the field, a single exam consisting of 200 questions taken over four hours, and a fee.
Informasi Silabus & Pendaftaran Hubungi
Purnama Academy
Whatsapp : 0838-0838-0001
Tuesday, September 13, 2022
WHAT IS POWER QUERY-PURNAMA ACADEMY TRAINING
High-quality analysis relies on well-organized data that is free from errors and that draws data from a single source of truth. Whilst many analysts spend hours of time manipulating data, combining data, and performing look ups, Power Query allows all of these steps to be automated with simple, repeatable steps.
Power Query is one of the most transformative tools available to any analyst working with data in Excel. Not only will it save analysts hours of time, but it will result in reduced manual errors and a better ability to source data from a single source of truth.
Informasi Silabus & Pendaftaran Hubungi
Purnama Academy
Whatsapp : 0838-0838-0001
Monday, September 12, 2022
WHAT IS PYHTON PROGRAMMING - PURNAMA ACADEMY TRAINING
Often, programmers fall in love with Python because of the increased productivity it provides. Since there is no compilation step, the edit-test-debug cycle is incredibly fast. Debugging Python programs is easy: a bug or bad input will never cause a segmentation fault. Instead, when the interpreter discovers an error, it raises an exception. When the program doesn't catch the exception, the interpreter prints a stack trace. A source level debugger allows inspection of local and global variables, evaluation of arbitrary expressions, setting breakpoints, stepping through the code a line at a time, and so on. The debugger is written in Python itself, testifying to Python's introspective power. On the other hand, often the quickest way to debug a program is to add a few print statements to the source: the fast edit-test-debug cycle makes this simple approach very effective.
Informasi silabus & pendaftaran Hubungi
Purnama Academy
Whatsapp : 0838-0838-0001
Friday, September 9, 2022
WHAT IS CISA ISACA-PURNAMA ACADEMY TRAINING
CISA affirms your credibility to offer conclusions on the state of an organization's IS/IT security, risk and control solutions.
CISA confirms to stakeholders your abilities to identify critical issues and recommend enterprise specific practices to support and safeguard the governance of information and related technologies.
CISA offers proof of your competency in IT controls and your understanding of how IT relates to business.
CISA assures your understanding of policies, standards, procedures, and controls to ensure the confidentiality, integrity, and availability of information assets.
Informasi silabus & pendaftaran Hubungi
Purnama Academy
Whatsapp : 0838-0838-0001
Wednesday, September 7, 2022
WHAT IS CRISC ISACA-PURNAMA ACADEMY TRAINING
Whatsapp : 0838-0838-0001
Tuesday, September 6, 2022
WHAT IS CGEIT ISACA - PURNAMA ACADEMY TRAINING
The exam consists of 150 multiple-choice questions and you'll have four hours to complete the in-person exam. Testing locations can be found through PSI Online and, depending on your location, you'll likely be able to choose between a testing center or a kiosk. At a testing center, you'll take a live proctored exam with other exam-takers, but at a kiosk location, you'll take the exam alone at a small work station in a "managed, yet self-service way." The ISACA offers more information on each testing experience to help you choose the best option for you.
[ Get ahead with the top certs for big data, project management, agile, data science, IT management and the cloud, as well as the top-paying certs and emerging certifications for today's hottest skills. | Get weekly career tips by signing up for our CIO Leader newsletter. ]
Exams are offered during three specific testing windows during the year — the first testing window in 2019 will run from February 1 to May 24. The two other testing windows for 2019 haven't been announced yet, but they typically run for three-month periods.
What's on the CGEIT exam?
The ISACA organizes the exam by five main CGEIT domains, which includes:
Domain 1: Framework for the governance of enterprise IT (25% of the exam)
Domain 2: Strategic management (20% of the exam)
Domain 3: Benefits realization (16% of the exam)
Domain 4: Risk optimization (24% of the exam)
Domain 5: Resource optimization (15% of the exam)
Domain 1 includes establishing a framework for governance of enterprise IT that helps the organization realize its goals and objectives, while considering risk and optimization. It also covers all the basic requirements, policies, principles, processes, organizational structures, infrastructure, skills and competencies necessary to build, oversee, and manage a framework IT governance.
Domain 2 focuses on aligning IT with enterprise objectives creating a strategic plan that helps the organization understand how changes to business strategy will impact IT strategy. This domain covers knowledge of IT roles and responsibilities, prioritization processes, documentation and communication methods, potential barriers for strategic alignment and current and future technologies.
Domain 3 covers benefits realization, which is the process of managing, tracking and reporting on the performance of IT investments to ensure they deliver optimized business benefits. This domain includes knowledge of KPIs, benefit calculation techniques, how to measure and monitor outcome and performance, and knowledge of continuous improvement concepts and principles.
Domain 4 encompasses risk optimization, which is the process of ensuring IT risk management frameworks help identify, analyze, mitigate, manage, monitor and communicate IT-related business risk and that they're aligned with the enterprise risk management (ERM) framework. Risk optimization also includes an understanding of appropriate legal and compliance regulations and the ability to communicate risk to senior-level executives. You'll need knowledge of disaster recovery planning (DRP), business continuity planning (BCP), standard risk management frameworks, key risk indicators (KRIs) and the skills to report on analytical data.
Domain 5 covers the optimization of IT resources, including information, services, infrastructure and applications, and people. This domain includes everything you need to know to ensure the correct processes are in place to reach enterprise goals. You'll need knowledge of IT resource management, service level agreements (SLAs), operation level agreements (OLAs) and data management and data governance.
For a more in-depth look at the tasks and knowledge areas for each domain, you can visit the ISACA website.
CGEIT qualifications
To qualify for the exam, you'll need at least five years of relevant work experience with one year working in Domain 1 (managing frameworks) and the other four years spent working in at least two out of the five other domains. You won't have to take a course to pass the CGEIT; instead your work experience and background serve as your CGEIT education. This certification is designed for professionals who have "significant management, advisory, or assurance role relating to the governance of IT and the knowledge required to perform these tasks," according to the ISACA
Purnama Academy
Whatsapp : 0838-0838-0001
Monday, August 29, 2022
Apakah itu COBIT 2019
COBIT memiliki 4 cakupan domain, yaitu:
Perencanaan dan organisasi (plan and organise)
Pengadaan dan implementasi (acquire and implement)
Pengantaran dan dukungan (deliver and support)
Pengawasan dan evaluasi (monitor and evaluate)
Maksud utama COBIT ialah menyediakan kebijakan yang jelas dan good practice untuk IT governance, membantu manajemen senior dalam memahami dan mengelola risiko-risiko yang berhubungan dengan IT.
COBIT menyediakan kerangka IT governance dan petunjuk control objective yang detail untuk manajemen, pemilik proses bisnis, user dan auditor.
Hubungi Purnama Academy 0838-0838-0001 untuk pendaftaran dan informasi detail silabus training tersebut di atas
Apakah CISM
Untuk mendapatkan sertifikasi CISM, kandidat harus melalui ujian tulis sertifikasi serta memiliki pengalaman paling tidak lima tahun di bidang keamanan informasi. Biasanya, profesional yang telah memiliki sertifikasi CISA atau CISSP juga berupaya mendapatkan sertifikasi CISM.
** Hubungi Purnama Academy 0838-0838-0001 untuk pendaftaran dan informasi detail silabus training tersebut diatas
Friday, June 17, 2022
TECHNICAL WRITER FOR SOFTWARE/ APPLICATION
HERY PURNAMA, SE.,MM.
MCP, PMP, CISM, CISSP, CISA, ITILF, CTFL, CDMP
CERTIFIED TRAINER - BANDUNG
081-223344-506
SILABUS TRAINING
Technical Writing for Software / Application
DURATIONS : 4 DAYS (OFF/ONLINE TRAINING 09.00 – 16.00 )
DESCRIPTION : Is the ability to provide relevant information about using your software essential for your customers? Do you find yourself spending hours and hours trying to explain how to use the software? Or are you getting feedback from your clients that your documentation is hard to be followed, inconsistent or maybe even.... confusing?
If you answered with "Yes!" to any of these questions and you are willing to invest the time and energy needed to go through this practical course then this course is for you!
A software technical writer creates documents to describe how to set up and use software products. Software technical writers make user guides, setup instructions, instruction manuals, online training material, release notes, new feature documents, how-to guides, and quick reference articles
TRAINING OBJECTIVES : This course is designed for beginner technical writers, usually students in IT, and covers the following subjects:
• What is technical writing / writer all about?
• What are the basics of Software technical writing?
• Which are the main principles that you should follow to construct build your documentation?
• Which are the common terms you will hear and use in the IT technical writing world?
• How to write technical documentation using GitHub wiki? You will, later on, use this material for creating your portfolio that you will want to add to your CV when you apply for a technical writer job or promotion to a senior developer.
• What is information architecture from a technical writing point of view?
REQUIREMENTS : You will need a PC or a laptop where you can develop content assignments or install particular software we will be using on trial basis in the course of the training
PARTICIPANTS : - Software developers who want to gain practical knowledge on how to offer help for the users of software products
- Students who work on their software development projects and now struggle to create the documentation delivery for their app
- If you pursue career as a technical writer, developer, architect, manager or product owner
- Business analysts who want to know the basics of technical writing
- Technical Writers and Information Developers
TRAINING TOPICS : Application Technical Writer Overview
What is Technical Writing
Who is Doing Technical Writing
What is the Result from Technical Writing
The Job of Technical Writer
Types of Documentation
Functional Documentation
Functional Documentation in Application Documentation
Strategy for writing functional Documentation
Task- Oriented Documentation
Srategy for writing task-Oriented Documentation
What is Application Documentation
Technical Writers in the Application Development World
Technical Writing Deliverables for Application
Documentation in the Application Development World
Technical Writer in the Application Development Team
The Technical Writing Process
The Ultimate Purpose of the Technical Writer
Test Your Knowledge Documentation in the Application Development World
Writing Documentation Using GitHub Wiki
Overview - Sample Setup in GitHub
What is GitHub?
Why Writing in GitHub?
Documentation in GitHub
Markup Language in Wiki Pages
Set up Account in GitHub and Create a New Wiki Page
How to Create a Table in GitHub Wiki Using Markdown
How to Create an Image in GitHub Wiki using Markdown
How to Create a Link to a Mail Address in GitHub Wiki Using Markdown
How to Create a Table of Content (TOC) in GitHub Wiki Using Markdown
Style Guide In Technical Writing
How to Use a Style Guide in Technical Writing
What is Style Guide?
Why do we Needs Standards for Writing?
Sample Style Guides
Who Else Needs Rules for Writing?
Results from Using a Style Guide
Structure in Writing
Conciseness
Simplicity
Precision
Verb Choice Can or May?
Verb Choice Must/Must not/Should/Shouldn't/May
Active Voice and Present Tense
Terminology
Consider in Addition
Use Tools!
UI Messages and Text on Screen
Introduction of Strurtured Writing
Structured Writing
Why Do We Need Structure in Writing?
Organizing Large Amounts of Content
Consistency in User Experience
Intuitive and Obvious User Experience
Ensuring Completeness of the Documentation
Targeting Content to Various Audiences
Coordinating Documentation Projects
Increase Understandability of the Documentation
Structured Writing Definition
Common Information Types
DITA XML - a Standard for Structured Writing
How to Structure in an Unstructured Writing Environment?
Structured Writing in Microsoft Word Environment
Details of the Topic Types in the MS Word Template
Structured Writing in GitHub Wiki
Details of the Topic Types in the GitHub Wiki Template
12 Principles of Technical Writing
Principles of Technical Writing
Principle #1 Decide Who are You Writing For
Principle #2 Identify the Information Needs
Principle #3 Decide on the Style
Principle #4 Decide Which Deliverables to Create
Principle #5 Decide Which Tools to Use
Principle #6 Define the Content Structure
Principle #7 Decide Which Information Channels to Use
Principle #8 Write the Documentation
Principle #9 Use Images and Video When Appropriate
Principle #10 Publish the First Version
Principle #11 Collect Feedback and Improve
Principle #12 Repeat!
Exercise on Applying the Principles in Documentation
Application Documentation Development using DITA XML (Oxygen Author)
What is DITA?
Who Defines DITA?
The DITA Specification
Overview of the Specification
Do You Need to Know the Specification by Heart?
Basics of Structured Writing
Understanding DITA Authoring Point of View
Understanding DITA Information Architect Point of View
How to Install the Application for This Section
Oxygen XML Author
Installing a Tool for Writing with DITA
End-to-end Demo
Exercise Write a Sample Instruction
Exercise Writing Documentation using Oxygen Author DITA CMS
Using Graphics & Images in Software Documentation
Why Graphics are Important?
When to Use Graphics in Application Documentation?
Types of Graphics in Application Documentation
Process Graphics
Architecture Graphics
Infographics
Rules for Graphics in Technical Writing
Tools for Creating Graphics
Exercise Instructions
Infographic Exercise - Expected Result
Demo - Create Infographic Using Canva
Creating Graphics Using Microsoft PowerPoint
Demo Using Microsoft PowerPoint
Exercise - Creating Graphics Using Google Drive
Strategies and Technical Writing Information Archictecture
What is Information Architecture?
Who is an Information Architect and What Does an IA Do?
Why Should I Care About Information Architecture?
Information Architecture in Technical Writing
How to Apply Information Architecture Principles for the Content?
Structuring Data. Metadata and Taxonomies.
What is Metadata?
What is Taxonomy?
Starting the Classification and Engaging Stakeholders
Define Scenarios
Visualize It!
Next Recommendation Training : 1. ISTQB CTFL Exam Preparation Training
2. Application Testing Automations with Katalon Studio & Jenkins
IT HELPDESK MANAGEMENT TRAINING, BY CERTIFIED TRAINER
HERY PURNAMA, SE.,MM.
MCP, PMP, CISM, CISSP, CISA, ITILF, CTFL, CDMP
CERTIFIED TRAINER - BANDUNG
081223344506
SILABUS TRAINING
IT HELPDESK MANAGEMENT
DURATIONS : 3 DAYS (OFF/ONLINE TRAINING 09.00 – 16.00 )
DESCRIPTION : Your IT Help desk is the center of your customer service team. It helps your business provide customer-centric service through automating and organizing their daily workflow. By doing correct IT Heldesk Management Practices and supplying employees with proper tools they need to quickly response and take actions for any issues and user questions, your company will creates a more powerful service cycle
TRAINING OBJECTIVES : This Course provide an overview of the typical knowledge and skills required, without focusing on any one technology vendor or platform.
This course does assume the participants already has some technical knowledge that will be utilized in a Help Desk role. The focus of the course is on the high-level Management practices that are important when providing Help Desk support services, including customer service, IT Service Management and the technical activities that will be performed.
The course material also is based on the ITSM best practices
You learn Incident and Request classification, specific features of performing major Incident resolving. You learn and practice on creating Incident and Request models for certain types of user calls.
While Monitoring/Event management studies You learn the best practices of building-in monitoring tools in an IT service, types of events, and management of them.
Problem management is mostly an expert area. At the course students learn and practice best practices of expert analysis such as mind maps, Kepner Tregoe analysis, Five Whys, and others.
REQUIREMENTS : • Junior experience at a Help desk/Service desk or other IT junior positions
• Basic knowledge in IT management
PARTICIPANTS : - Service Desk/Help desk specialists
- Service/Help desk managers
- IT managers
- Business unit managers which closely collaborate with IT departmen
TRAINING TOPICS : IT Helpdesk Management Overview
What is IT Helpdesk Management
IT Helpdesk Vs IT Service Desk
IT Helpdek Hiring Management Practice
Hiring New Staff & Smart Hiring
To DO List, Expectations, Technical Skills and Attributs
Have Others Check your List, Legally Complaint, Chart Review and Essentials
Create Job Description and Get the Word Out
Narrow your Application Pool, Prepare for the Interview and Resources
Know Who you are Talking To, Asking the Right Questions, About Discrimination
Open-ended, Relevant to the Position and the Individual & The Interview
Evaluation, In Review, Background Check, Extend the Offer & Steps in Hiring
Topgrading
Introduction and Definition of Topgrading
Definition of A-players, Best of the Rest and Appropriate Compensation
The Big Question, Implementation, Best Practices, Talent Review and Scorecards
Interview Process and Types of Interview
It Helpdesk Team Building
Working in a Team, Types of Team and Teamwork Success
Employee Involvement, Team Conflict and Team Leaders Role in Managing Conflict
Leadership, Learning to be a Leader, LEAD Model & What Sort of a Leader are You
Lead by Example and Management Process
How to Motivate, Coaching Staff and Coaching Skills
Working Together, Why is Training Needed and Contributing to the Team
Learning Organizations, Development Cycle and Performance Appraisals
Cross Training and Poor Management
Managing Your IT Helpdesk Team
Introduction, All About Money, and Reward and Recognition
The Cost, Factors, Challenging Goals and Clear Instruction
Meaningful Tasks, Feedback, Rewards and Incentives
No Single Rewards, Who Benefits and The Bottom Line
Performance Reviews and Avoidance
Tips for a Better Performance Review and Signs of Success
Retention of Quality, What can We Do, Research and Best Workplaces
Motivational Strategies, Rates, Most Important Attributes & Collecting Feedback
Ask, Cluster Surveys, Started Feedback, Stay and Exit Interview Survey
IT Service Management Principles
Introduction, Definition and Good Practice for ITSM?
Business, IT Alignment, Definition of Services and Process & the Generic Process
Function and Process Owner vs Service Owner
Service Lifecycle
IT Financial Management
Demand Management
Request Fulfillment
Access Management
Service Operations Process
INCIDENT Management & tasks
Problem management
Problem management assignment
Event management - Service monitoring and control
Serving user requests (RFS)
Develop a Request model
Selecting A Help Desk Tools
Importance of Supporting Technology, Common Features and Additional Features
Selection Process and Knowledge Management Integration
Workflow Management and Major Tool Vendors
IT Helpdesk Support Services
How to Properly Trouble Shoot PC Issues
How to Properly Trouble Shoot Printer Issues
Screen Sharing with Team Viewer
Active Directory Users and Computers Demostrated and explained
Introduction to Microsoft Outlook
Common Password Locations : Credential Manager
Common Password Locations : Google Chrome
Commong Password Locations : Wifi
What is the Internet
Basic Networking : IPconfig, Ping, Pathping
Next Recommendation Training : 1. ITIL V.4
2. ISO 20000 IT Service Management (ITSM)
3. ICT Governance
SOFTWARE QUALITY ASSURANCE (SQA) TRAINER
HERY PURNAMA, SE.,MM.
MCP, PMP, CISM, CISSP, CISA, ITILF, CTFL, CDMP
CERTIFIED TRAINER - BANDUNG
SILABUS TRAINING
SOFTWARE QUALITY ASSURANCE (SQA)
DURATIONS : 4 DAYS (OFF/ONLINE TRAINING 09.00 – 16.00 )
DESCRIPTION : This program is designed for Software Quality Control and Assurance Manager, Project Manager and Software Development Team Member who is interested in increasing the likelihood of project success. The course looks at software quality control and assurance processes and practices, as well as support disciplines such as software project management, software configuration management and release management. Successful software quality assurance is the result of the combination and integration of these practices, and complements SE practices.
TRAINING OBJECTIVES : • Write a software quality plan
• Define software quality metrics
• Prepare software quality checklists
• Develop an overall process improvement plan
• Understand how to best help your colleagues with the quality of their outputs
• Ensure the highest possible quality products
• Deliver value-added products
• Help your company win more business by delivering higher quality
REQUIREMENTS : Have a general knowledge of software development life cycles.
Does not require knowledge of any programming languages
PARTICIPANTS : - Learners and practionares of quality control, quality assurance and quality management.
- software developers
- software project managers and team leaders
- Example: Beginner level course ideally suited for someone who knows very little about software quality assurance
TRAINING TOPICS : Chapter 1 Quality Assurance Basics
Connotations of the Word Quality
What Is Quality?
Specifications
Definition of Quality from the Standpoint of the Provider
Quality and Reliability
Evolution of the Concepts of Quality
Quality Gurus
Total Quality Management
Are We Giving Adequate Importance to Quality in Organizations?
Organizational Goals and Quality Goals
Is a Quality Department in Software Development Organizations Really Needed?
The Present Scenario in Software Development Organizations
Chapter 2 Four Dimensions of Quality
Background
Specification Quality
Design Quality
Development (Software Construction) Quality
Conformance Quality
Ensuring Quality in Specifications
Ensuring Quality in Design
Ensuring Quality in Development (Software Construction)
Ensuring Conformance Quality
Chapter 3 Software Product Quality
Functionality Standpoint
White Box (Glass Box) Standpoint
Presence of Defects in the Product
Program Quality
Measurement of Product Quality
Chapter 4 Organizational Environment that Fosters a Quality
Culture
Quality and Organizational Environment
Need for an Independent Quality Assurance Department
The Role of the Quality Assurance Department
The Position of the Quality Assurance Department in an Organization
Organization of the Quality Assurance Department
Organization and Staffing of the Quality Assurance Department
A Well-Defined and Institutionalized Software Development Process
Explicit System of Rewards and Recognition for Achieving Excellence in Quality
Commitment and Involvement of Senior Management in Fostering a Culture of Quality in the Organization
Chapter 5 Software Verification
Verification
Walkthroughs (Peer Reviews)
Inspections
Audits
Verification Process
Implementation of Verification Activities in Projects
Chapter 6 Validation
Definition of Validation
Validation of Software Designs
Validating the Product Specifications
Validating the Software Product
Testing Different Types of Software Products
Testing Basics
Approaches to Testing
Test Case Design
Test Environment
Testing Scenarios
Project Testing or Embedded Testing
Product Testing
Best Practices in Testing
Automation of Testing and Use of Testing Tools
Final Words about Software Testing
Chapter 7 Software Product Quality: Reliability
Software Disasters
Software Reliability
Cause of Software Failures
Prediction of Software Reliability
Software Reliability Improvement
Chapter 8 Process Quality
Process Quality Evolution
Aligning the Process with a Process Model
Process Improvement
Process Stabilization
Software Development Process
Components of a Process
Process Certification
Chapter 9 New Paradigm for Software Quality
Current Certification Paradigms
The Fallacy of Certifications
Criticisms of Maturity Models
A New Paradigm for Software Quality Assurance
Next Recommendation Training : 1. ISTQB CTFL Exam Preparation Training
2. Software Testing Automations with Katalon Studio & Jenkins
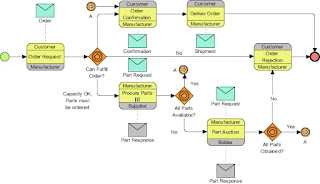
BUSINESS PROCESS MODEL TRAINER - BPMN TRAINING
HERY PURNAMA, SE.,MM.
MCP, PMP, CISM, CISSP, CISA, ITILF, CTFL, CDMP
SILABUS TRAINING
BUSINESS PROCESS MODEL WITH BPMN
DURATIONS : 4 DAYS (OFF/ONLINE TRAINING 09.00 – 16.00 )
DESCRIPTION : Business process modeling in business process management and systems engineering is the activity of representing processes of an enterprise, so that the current business processes may be analyzed, improved, and automated
TRAINING OBJECTIVES : • Create clear, correct and expressive BPMN 2.0 Models with clear process logic
• The full vocabulary of BPMN 2.0 Level 1: the descriptive modelling pallet
• The context of BPMN, BPM and Business Analysis in general
• Best practices approach with tips and tricks to model any real-world process
• How to improve real-world processes using BPMN 2.0
• How to adhere a common modelling method to create consist diagrams for both Business and IT
REQUIREMENTS : This training is tool independent, just like BPMN itself. You can use your own tool or use the free web-based one
PARTICIPANTS : - Business Analysts
- Aspiring Business Analyst
- Managers
- Technical Developers
- Consultants
- External teams and third parties
- Process Improvers
TRAINING TOPICS : Introduction to BPMN
What is BPMN
Practice the core elements
The Advantages of BPMN .
BPMN . versus Traditional Flowcharts
BPMN . and BPM Suites
Why BPMN . is Important
Getting Started with BPMN
Tooling BPMN . Setup & Tips and Tricks
BPMN for Practitioners
Model your First BPMN
Using XOR Gateways correctly
Practical Example Model a webshop order proces.
Practice with XOR gateways and conventions
Pools, Lanes, Subprocess, Hierarchical Model
Pools in BPMN
How To Creating Pools in Lucidchart
Lanes and Pools in BPMN
How To Create Lanes in Lucidchart & replicate the model
Different Task Types User and Service
Subprocesses, Nesting and Inline or Hierarchical Expansion
Parallel Gateways, Terminate End Events and Timer Trigger Events
Collaborations, Message Flows, data Objects & Events
Collaboration, Blackbox pools, message events & Flows
Collaborations in practice
Data Objects, Data Stores and Call Activities
Annotation Options in BPMN
Exercise Practice with Message End Events
Summary the All of Elements
Starts & Events
Activities and subprocesses
Gateways, Connectors. Pools, lanes and black boxes
Data objects
Annotation
Quality, Best Practices and Methodology
About Good BPMN
Seven Best Practices to create good BPMN . Models
Agile methodology to go from a blank piece of paper to a full BPMN diagram
Practice & Case Study
Business Case Assignment Description
Business Case The Scenario
Step 1 Assignment Scope of the high level Business Process
Step 1 Solution Scope the high level business process
Step 2 Part I Assignment Model the happy path scenario
Step 2 Part I Solution of the happy path scenario
Step 2 Part I How to draw the happy path scenario Lucidchart
Step 2 Part II Assignment Add exception flows
Step 2, Part II Solution of adding the exception flows
Step 2 , Part II How to model the exception flows in Lucidchart
Step 2, Part III Assignment Add all detail to the high level process
Step 2, Part III Solution of Adding all detail to the Model
Step 2 , Part III How to add all detail to the model in Lucidchart
Step 3 Improve The Process
Step 3 Assignment Model the improvement
Step 3 Solution
Step 3 How to model 'to be' or 'target' business process models
Step 4 Scope sublevel processes; scenario and assignment.
Step 4 Solution of scoping the sublevel processes
Step 5 Model subprocesses assignment
Step 5 Solution of the subprocess
Step 5 How to model the subprocess in Lucidchart.
Next Recommendation Training : 1. S.A.D with UML
2. Enterprise Architect with TOGAF 9
IT CYBER RISK SECURITY MANAGEMENT TRAINER
HERY PURNAMA, SE.,MM.
MCP, PMP, CISM, CISSP, CISA, ITILF, CTFL, CDMP
CERTIFIED IT TRAINER - BANDUNG
SILABUS TRAINING
IT CYBER RISK SECURITY MANAGEMENT
DURATIONS : 3 DAYS (OFF/ONLINE TRAINING 09.00 – 16.00 )
DESCRIPTION : In this course you will gain a solid understanding of risk management principles, processes, frameworks and techniques that can be applied specifically to cyber security as well as risk in general.
You will learn how to identify, assess and articulate risk as well as options available for treating cyber security risk and which may be most appropriate for your situation.
This course also provides examples of tools and techniques as well as useful tips that can help you to successfully implement and maintain a risk management framework within your organization
TRAINING OBJECTIVES : • Develop an understanding of what risk is and how it can be managed.
• How to create a risk management framework within your organisation.
• How to identify, assess and articulate risk as well as identifying options for treatment and determining which is the most appropriate.
• How to perform detailed analysis of risk and develop risk treatment plans.
• How to apply risk management concepts in practice including developing a risk register, Cyber Security Strategy Plan, governance models, risk bowties and reporting.
REQUIREMENTS : No special requirements
PARTICIPANTS : - Information Technology Managers
- Information/Cyber Security Managers
- Information Security Professionals
- Anyone with an interest in gaining a general understanding of risk management as well as how it applies to information security
TRAINING TOPICS : Introduction
What Is Risk?
IT & Cyber Security Risk
Components of a Risk
Articulating Risk
Risk Management
What is Risk Management
Objectives of Risk Management
Risk Management vs Risk Minimisation
Risk Management Principles
Risk Management Framework
Mandate & Commitment
Designing your framework
Designing your framework – Organisational Context
Designing your framework - Establish Policy
Designing your framework - Accountability
Designing your framework - Organisational Integration
Designing your framework - Communication & Reporting
Designing your framework - Implementation
Designing your framework - Monitoring & Review
Designing your framework - Continual Improvement
The risk management process
The risk management process - Communication & Consultation
The risk management process - Context Establishment
The risk management process - Risk Assessment
The risk management process - Risk Treatment
The risk management process - Monitoring & Review
The risk management process - Auditability and Traceability
Risk Management - Maturity Models
Risk Management - Risk Assessment & Measurement
Risk Assessment & Measurement - Terminology
The risk management process (recap)
Risk Identification
Risk Analysys
Risk Analysis - Likelihood
Risk Analysis - Consequence/Impact
Risk Analysis - Consequence Examples
Risk Analysis - Risk Matrix
Risk Analysis - Analysis Example
Risk Evaluation
Risk Treatment
Risk Treatment Plan Example
Risk Treatment Considerations
Cyber Security Risk management in Practice
Creating an IT risk register
Example Excel risk register
Risk governance - lines of defence model
Developing Cyber Security Strategy Plan
Risk bowties
Next Recommendation Training : 1. CISM Exam Preparation Training
2. CISSP Exam Preparation Training
3. ISO 27001 Training
4. ISO 31000 Training
Top Topics
-
EXCEL DASHBOARD WITH POWERPIVOT AND POWERVIEW www.purnamaacademy.com , Hotline (Call/SMS/WA) : 0838-0838-0001 Syllabus Overview...
-
Purnama Academy 0838-0838-0001 Menyediakan training EXCEL DASHBOARD di Bandung, Jakarta, Surabaya , Yogya, Bali dan hampir seluruh wilayah ...
-
Materi Silabus Pelatihan ISTQB (International Software Testing Qualification Board) Training diselenggarakan oleh Purnama Academy 0838-0838-...
-
EXCEL VBA MACRO PROGRAMMING www.purnamaacademy.com , Hotline (Call/SMS/WA) : 0838-0838-0001 Syllabus Overview Training Ini ...
-
MySQL Cluster Syllabus Class Type : Training Duration : 5 Days (09.00 – 16.00) Training Description : Setelah mengambil ku...
-
Materi Silabus Pelatihan BUSINESS ANALYSIS WITH BABOK V.2 Training diselenggarakan oleh Purnama Academy 0838-0838-0001 dan berikut silabus ...
-
PHP AJAX JQUERY Class Type : Training Duration : 3 Days (09.00 – 17.00) Training Description : Look...
-
POWER BI PRO FUNDAMENTAL www.purnamaacademy.com , Hotline (Call/SMS/WA) : 0838-0838-0001 Syllabus Overview Training Ini akan ...